Image Access Management
Estimated reading time: 7 minutes
Image Access Management is a new feature that is a part of the Docker Business subscription. This feature allows Organization owners to control which types of images (Docker Official Images, Docker Verified Publisher Images, Community images) their developers can pull from Docker Hub.
For example, a developer, who is part of an organization, building a new containerized application could accidentally use an untrusted, community image as a component of their application. This image could be malicious and pose a security risk to the company. Using Image Access Management, the Organization owner could ensure that the developer can only access trusted content like Docker Official Images, Docker Verified Publisher Images, or the Organization’s own images, preventing such a risk.
Configure Image Access Management permissions
The following video walks you through the process of configuring Image Access Management permissions.
Detailed instructions
To configure Image Access Management permissions, perform the following steps:
- Log into your Docker Hub account as an organization administrator.
-
Select an organization, and navigate to the Settings tab on the Organizations page and click Org Permissions.
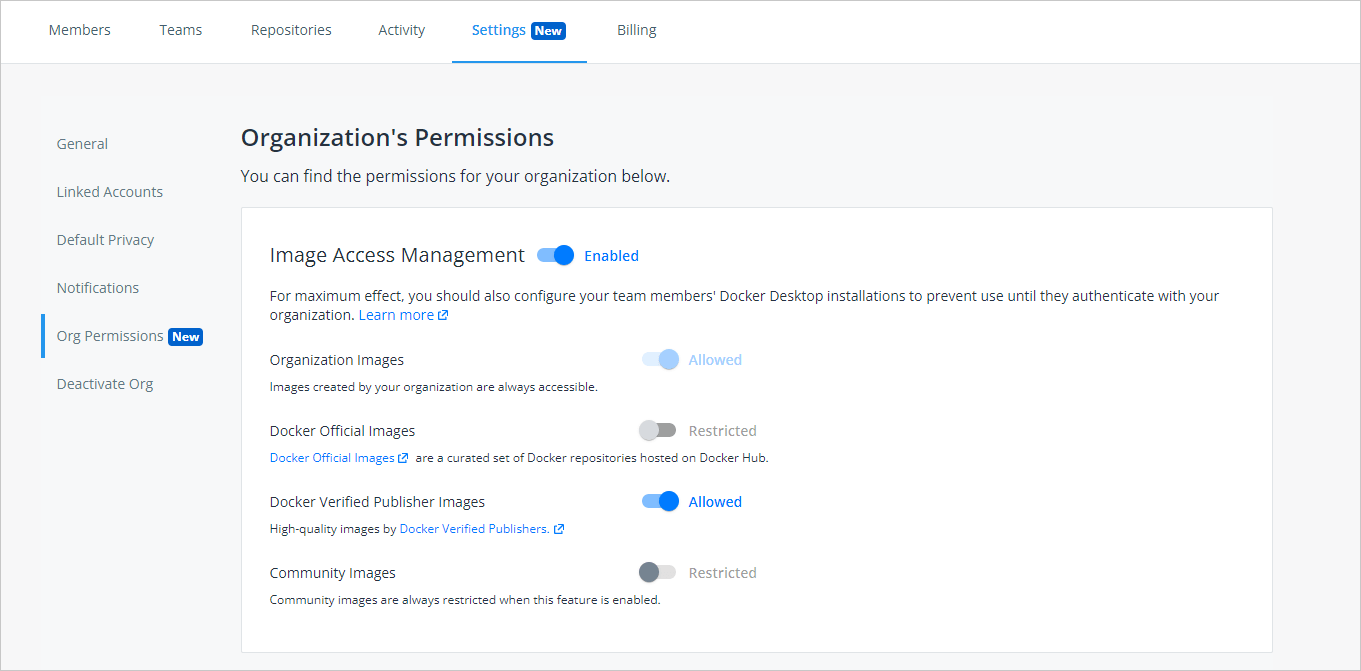
- Enable Image Access Management to set the permissions for the following categories of images you can manage:
- Organization Images: When Image Access Management is enabled, images from your organization are always allowed. These images can be public or private created by members within your organization.
- Docker Official Images: A curated set of Docker repositories hosted on Hub. They provide OS repositories, best practices for Dockerfiles, drop-in solutions, and applies security updates on time.
- Docker Verified Publisher Images: published by Docker partners that are part of the Verified Publisher program and are qualified to be included in the developer secure supply chain. You can set permissions to Allowed or Restricted.
- Community Images: Images are always disabled when Image Access Management is enabled. These images are not trusted because various Docker Hub users contribute them and pose security risks.
Note
Image Access Management is set to Disabled by default. However, member(s) of the
ownersTeam in your Organization have access to all images regardless of the settings. - Select the category restrictions for your images by clicking Allowed.
- Once the restrictions are applied, your members can view the Org permissions page in a read-only format.
Enforce authentication
To ensure that each org member uses images in a safe and secure environment, you can perform the following steps below to enforce sign-in under your organization. To do this:
- Download the latest version of Docker Desktop, and then
- Create a
registry.jsonfile.
Download Docker Desktop 4.0 or a later release.
Note
There is currently no Docker Desktop for Linux. Linux users will have the same restrictions as Mac and Windows users while logged in. However, there is currently no way to enforce Linux users to log in.
Create a registry.json file
When creating a registry.json file, ensure that the developer is a member of
at least one organization in Docker Hub. If the registry.json file matches at
least one organization the developer is a member of, they can sign in to Docker
Desktop and access all their organizations.
Windows
On Windows, you can run a command in a terminal to install Docker Desktop, or you can download Docker Desktop and manually create your registry.json file.
Run the following command in a terminal to install Docker Desktop:
C:\Users\Admin> "Docker Desktop Installer.exe" install
If you’re using PowerShell, you should run it as:
PS> Start-Process '.\win\build\Docker Desktop Installer.exe' -Wait install
If using the Windows Command Prompt:
C:\Users\Admin> start /w "" "Docker Desktop Installer.exe" install
The install command accepts the following flag:
--allowed-org=<org name>
This requires the user to sign in and be part of the specified Docker Hub organization when running the application. For example:
C:\Users\Admin> "Docker Desktop Installer.exe" install --allowed-org=acmeinc
To manually create a registry.json file:
- Open Windows PowerShell and select Run as Administrator.
- Type the following command
cd /ProgramData/DockerDesktop/ -
Type
notepad registry.jsonand enter the name of the Docker Hub organization that the developer belongs to in theallowedOrgskey and click Save. For example:{ "allowedOrgs": ["myorg"] }
This creates the registry.json file at C:\ProgramData\DockerDesktop\registry.json and includes the organization information the user belongs to. Make sure this file can’t be edited by the individual developer, only by the administrator.
Mac
On macOS, you can run a command in a terminal to install Docker Desktop, or you can download Docker Desktop and manually create your registry.json file.
Download Docker.dmg and run the following commands in a terminal to install Docker Desktop in the Applications folder:
$ sudo hdiutil attach Docker.dmg
$ sudo /Volumes/Docker/Docker.app/Contents/MacOS/install
$ sudo hdiutil detach /Volumes/Docker
The install command accepts the following flags:
--allowed-org=<org name>
This requires the user to sign in and be part of the specified Docker Hub organization when running the application. For example:
$ sudo hdiutil attach Docker.dmg --allowed-org=acmeinc
To manually create a registry.json file on macOS, you must create a file at /Library/Application Support/com.docker.docker/registry.json with file permissions that ensure that the developer using Docker Desktop cannot remove or edit the file (that is, only the system administrator can write to the file). The file must be of type JSON and contain the name of the Docker Hub organization names in the allowedOrgs key.
To create your registry.json file:
- Navigate to VS Code or any text editor of your choice.
-
Enter the name of the Docker Hub organization that the developer belongs to in the
allowedOrgskey and save it in your Documents. For example:{ "allowedOrgs": ["myorg"] } -
Open a new terminal and type the following command:
$ sudo mkdir -p /Library/Application\ Support/com.docker.dockerIf prompted, type your password associated with your local computer.
- Type the following command:
$ sudo cp Documents/registry.json /Library/Application\ Support/com.docker.docker/registry.json
This creates the registry.json file at /Library/Application Support/com.docker.docker/registry.json
and includes the organization information the user belongs to. Make sure this file
can’t be edited by the individual developer, only by the administrator.
Verify the restrictions
To confirm that the restrictions are successful, have each org member pull an image onto their local computer after signing into Docker Desktop. If they are unable to sign in, they will receive an error message.
For example, if you enable Image Access Management, your members can pull an Organization Image, Docker Official Image, or Verified Publisher Image onto their local machine. If you disable the restrictions, your members can pull any image, including Community Images.